Vulnerability Verification
Advertisement
Metasploit v.4. 1. 2004
The Metasploit Framework is both a penetration testing system and a development platform for creating security tools and exploits.
Advertisement
Image Verification Service ( CAPTCHA )
You needed to paste Single line Java script code, will Initiate CIS Image verification Engine to generate CAPTCHA Image using "Random Numbers, Characters and Background" and will place it on your webpage automatically. It do not have its own Submit button
.NET Framework Setup Verification Utility v.20-02-2010
This .NET Framework setup verification tool is designed to automatically perform a set of steps to verify the installation state of one or more versions of the .NET Framework on a computer. It will verify the presence of files, directories,
Free Fingerprint Verification SDK v.1.0
Freeware SDK and components for biometrical application development for Windows platform. Most suitable for developing biometrical logon applications. Allows reading fingerprints only from scanners, storing up to 10 fingerprint records in an
Application Service Level Vulnerability Assessment Test for .NET v.3.95
Conduct internal software audits for Microsoft.NET based Web applications to validate software quality and compliance with service level requirements.
Application Service Level Vulnerability Assessment Test for Java v.3.97
Conduct internal software audits for Java-based Web applications to validate software quality and compliance with service level requirements.

Verification Engine
VerificationEngine (VE) is an innovative free multi-browser anti-phishing & identity assurance tool to help consumers achieve a new level of online transactional security two ways. First, it helps consumers differentiate between good business-verified
Vulnerability Scanning Cluster v.2.0
The VSC is a PHP/MySQL/Apache Interface for Nessus 2.
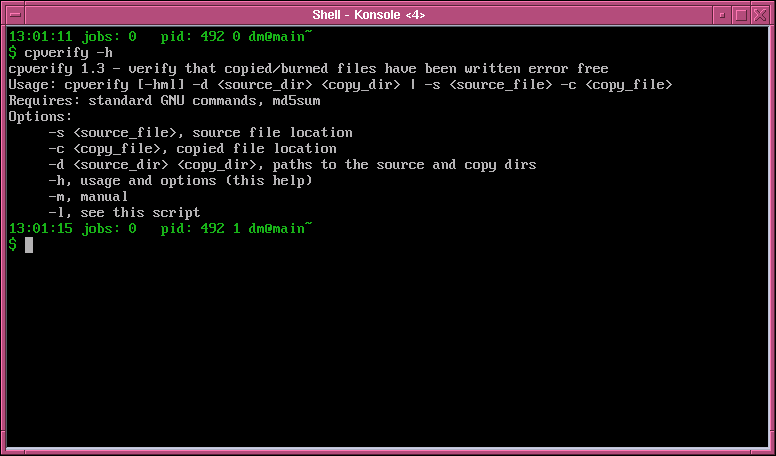
Backup verification tool v.1.3
cpverify verifies that a file or directory structure has been copied or burned without errors.
Quttera
Quttera is a Signatureless Malicious Content Detection Solution designated especially to identify the potentially malicious executable code, zero-day vulnerability exploit and shellcode embedded into computer files such as movies, images, documents and
ICE ECC
ICE ECC is a file verification and repair tool. ICE ECC allows you to protect your important files and sensitive data against digital corruption using Reed-Solomon codes. Did you know that a typical CD-R/DVD-R disk can hold its data intact for only